TUCTF 24
TUCTF Forensics Writeup
Challenge 1: Mystery Presentation
Challenge Description
- We recently received an absolutely non-sensical presentation from a confidential informant.A note was attached, stating: “The truth hurts boomers, but it’s what on the inside that counts <3”.We can’t make sense of it, but it must be important! Can you help us out?
Solution
- We are provided with a
.pptxfile and need to uncover the hidden flag.
- Identify File Type:
First, determine the file type using the
filecommand:1 2
file quantum_propulsion_via_dank_memes.pptx quantum_propulsion_via_dank_memes.pptx: Zip archive data, at least v2.0 to extract, compression method=deflate
This confirms that the PowerPoint file is essentially a ZIP archive.
- Extract Contents:
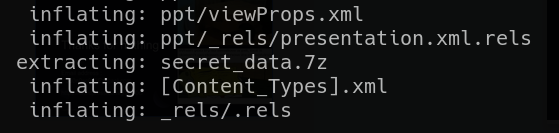
- Running the
stringscommand on the .pptx file revealed a hidden 7z file.
- I extracted the
secret_data.7zfile from the PowerPoint ZIP archive.
- Running the
- Extract the 7z File:
Using the following command, I extracted the contents from the 7z archive:
1
7z x secret_data.7z
This extraction revealed a flag.txt file.
- Reveal the Flag:
Using
cat, I displayed the contents offlag.txt:1 2
cat flag.txt TUCTF{p01yg10+_fi1e5_hiddin9_in_p1@in_5i9h+}
Polyglot files are pretty cool! Here are some more advanced ones:
https://github.com/angea/pocorgtfo
Flag
1
TUCTF{p01yg10+_fi1e5_hiddin9_in_p1@in_5i9h+}
Challenge 2: Packet Detective
Challenge Description
- You are a security analyst given a PCAP file containing network traffic. Hidden among these packets is a secret flag that was transmitted. Your task is to analyze the PCAP file, filter out common traffic, and pinpoint the packet carrying the hidden flag.
Solution
- We are given a
.pcapfile. - I opened the given traffic_analysis.pcap file in Wireshark.
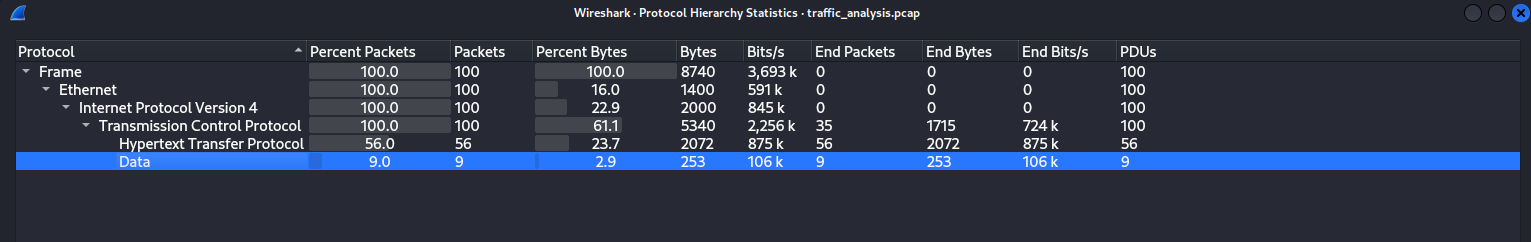
Navigated to:
1
Statistics → Protocol Hierarchy
From the analysis, I observed that HTTP traffic was present.
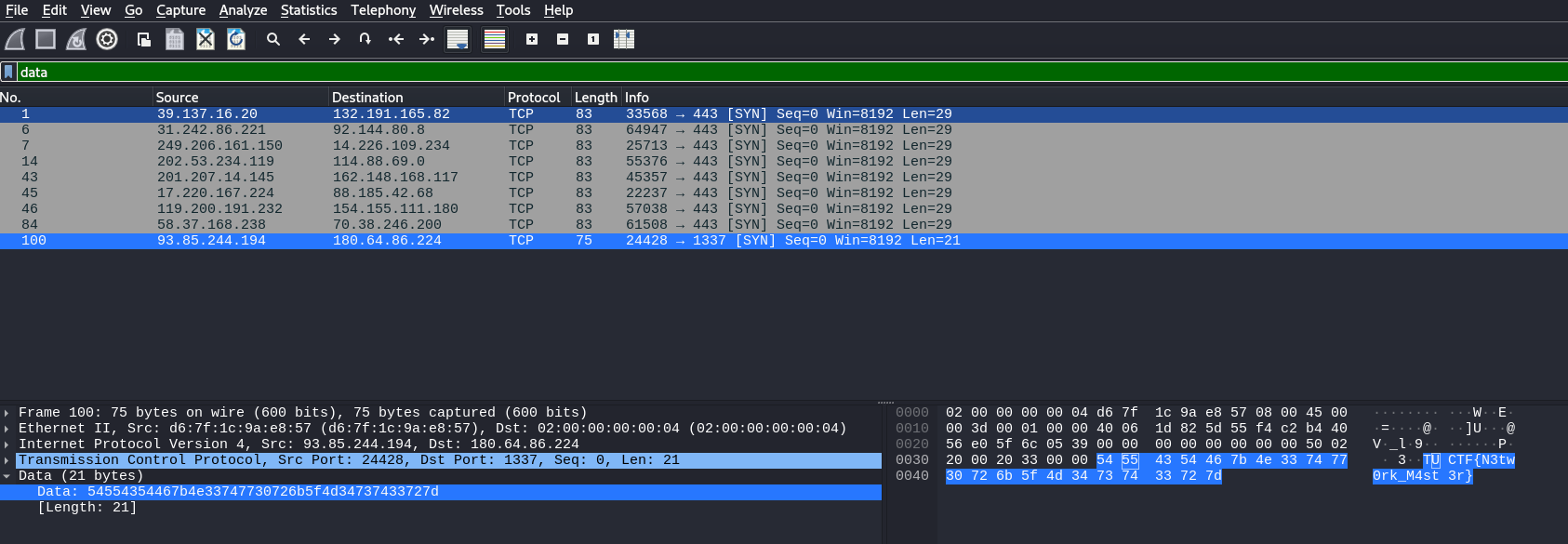
Since HTTP traffic often includes plaintext data, I applied the following filter to isolate relevant packets:
1
data
By examining the last data packet, I found the flag embedded within the transmitted content.
Flag
1
TUCTF{N3tw0rk_M4st3r}
Challenge 3: Bunker
Challenge Description
- [REPORT] Mail notification received from an access point.
- Subject:
YoRHa_CLASSIFIED_12u3440029491 - Origin:
Bunker
- Subject:
- Query: What is the nature of this transmission?
- Hypothesis: A deeper analysis of the enclosed files may yield more information.
- Proposal: The scanner-type unit is advised to perform standard scanning procedures on the data for further analysis.
- Warning: Data appears classified. Any unauthorized actions could be considered treason. Proceed in secrecy.
Solution
We are given with a .7z file
- Extract the Archive Contents
Extract the
.7zfile using7z:1
7z x Bunker.7z
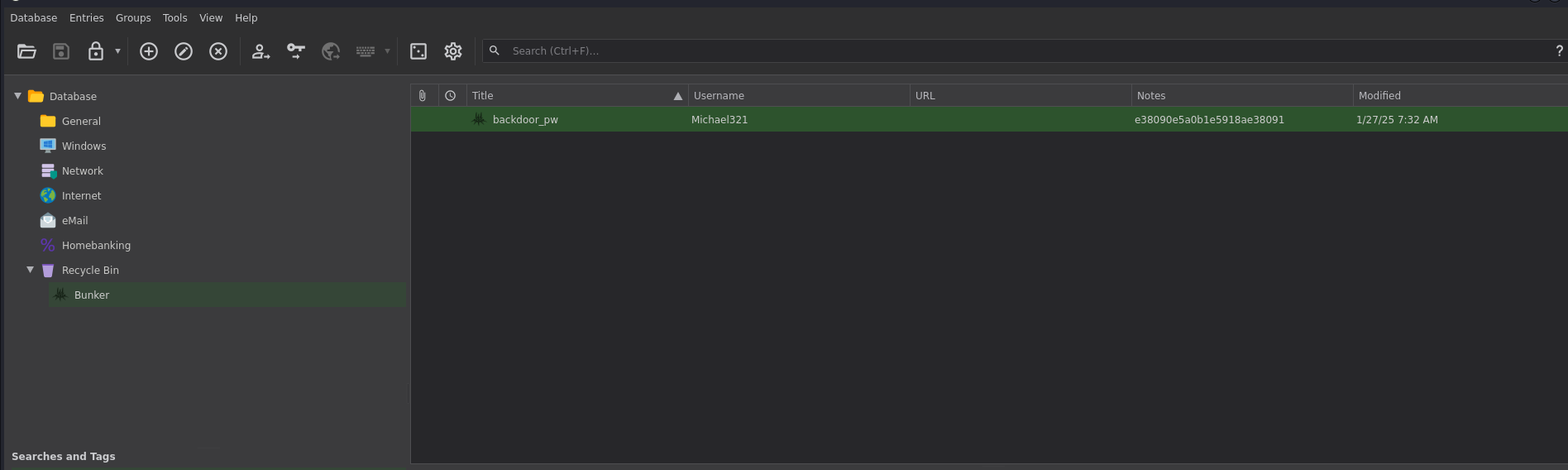
- This reveals two files:
Bunker_DB: Keepass password database (KDBX format)Bunker_DMP: MiniDump crash report
Confirming file types using the
filecommand:1
file Bunker_DB Bunker_DMP
Output:
1 2
Bunker_DB: Keepass password database 2.x KDBX Bunker_DMP: MiniDump crash report, 17 streams, Sun Nov 17 22:47:09 2024, 0x621826 type
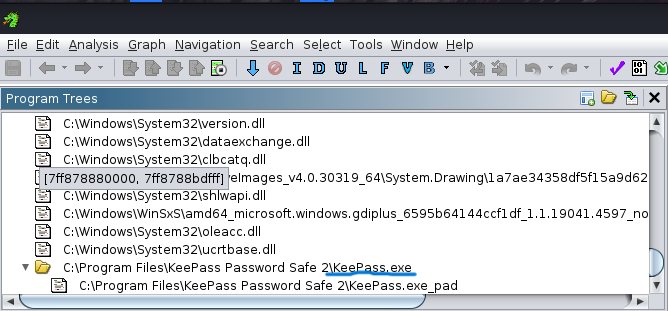
- Memory Dump Analysis
- Exploring KeePass Vulnerabilities
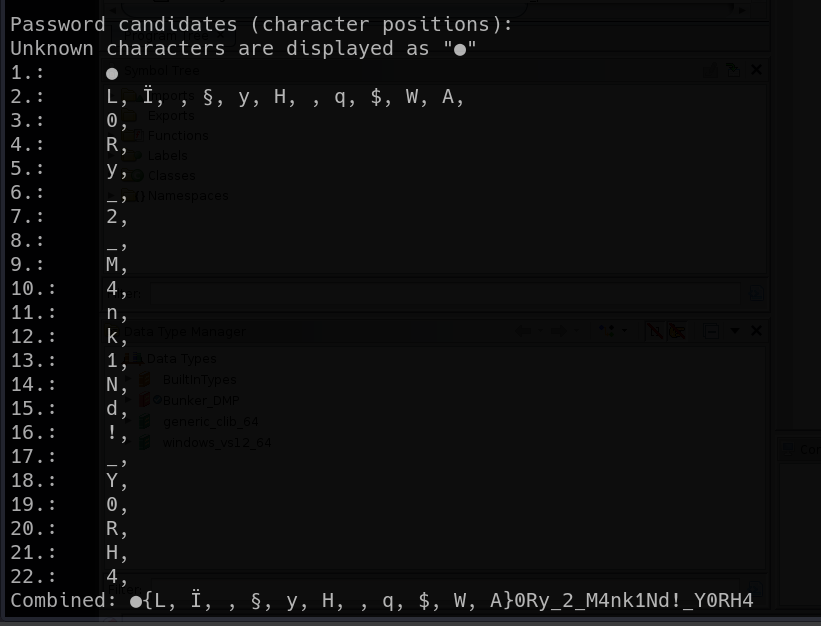
Researching KeePass vulnerabilities, we found CVE-2023-32784, which allows extracting the master password from memory dumps.
We cloned the following PoC exploit from GitHub:
1
https://github.com/vdohney/keepass-password-dumper
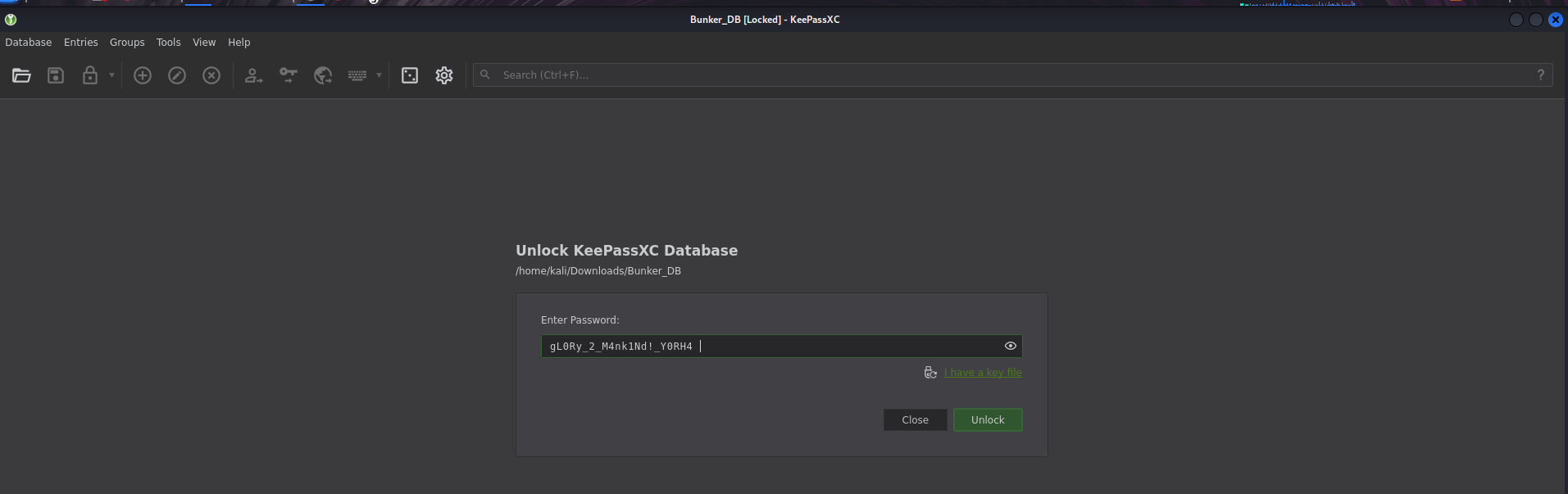
- Extracting the KeePass Master Password
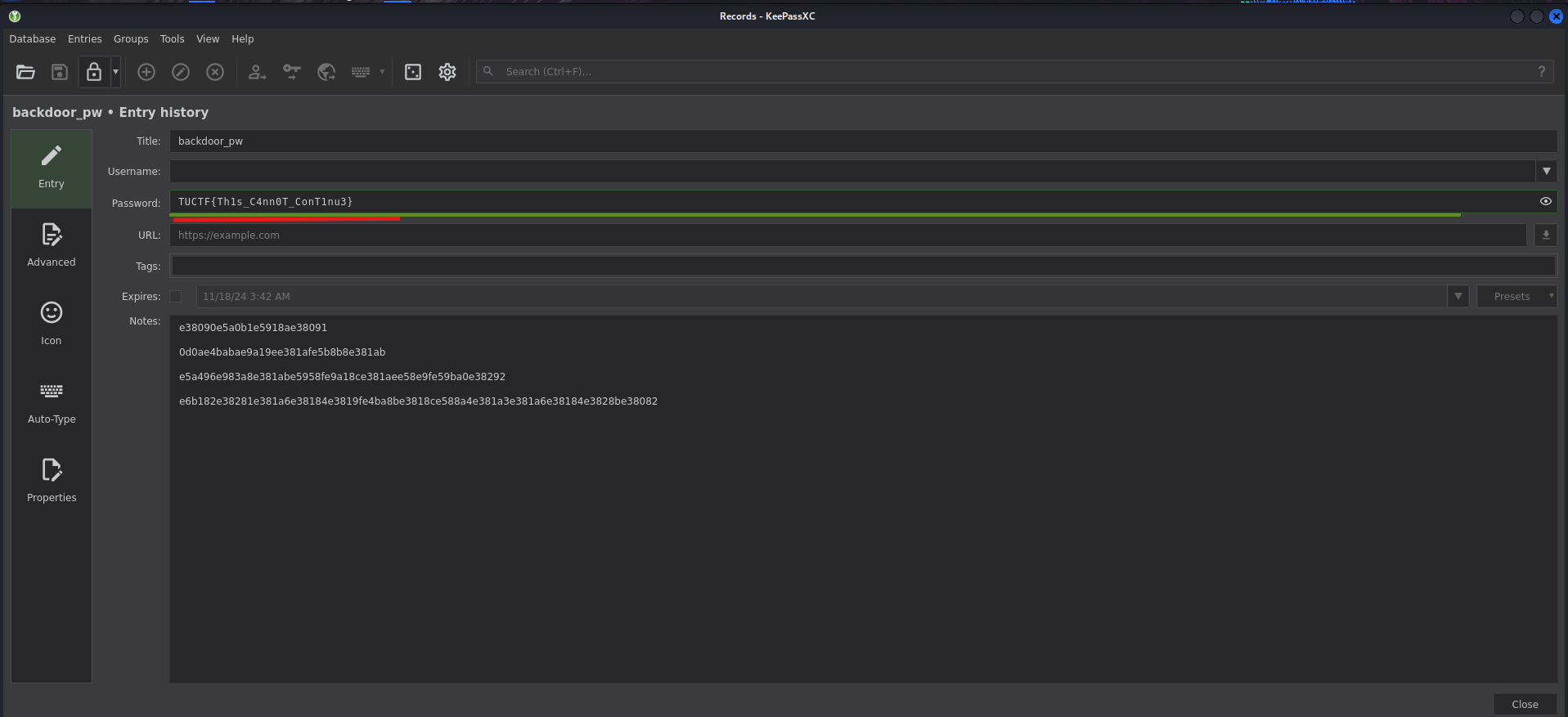
- Unlocking the KeePass Database
- Exploring the KeePass Entries
Flag
1
TUCTF{Th1s_C4nn0T_ConT1nu3}